Did you know blockchain isn’t truly bulletproof despite its reputation for ironclad security? As blockchain technology revolutionizes industries from finance to healthcare, its growing adoption brings a stark reality: security issues are rising. Smart contracts and network protocol vulnerabilities pose significant blockchain risks, threatening data and assets.
This article reveals critical blockchain security issues in today’s software projects. It also shows how strategic blockchain testing services can be your strongest defense, ensuring reliable blockchain solutions.
Why Security Is Vital in Blockchain Development
The inherent characteristics of blockchain technology—decentralization, immutability, and transparency—make security a necessity. Blockchain security isn’t just about coding; it’s about maintaining users’ money, privacy, trust, and growth. The following key factors underscore why blockchain security needs to be a top priority throughout the development lifecycle.
Permanence of Errors
One of blockchain’s defining features is its immutability, meaning the data cannot be altered once recorded. While this is a strength against tampering, it becomes a critical vulnerability if unauthorized transactions or destructive smart contract codes are embedded into the chain.
This immutability raises the stakes for security, demanding careful attention to detail and bold threat mitigation. Powerful security measures are essential to prevent harmful actions or coding errors from becoming irreversible.
Big Money Meets Big Risks
Blockchain systems frequently manage cryptocurrencies and a growing collection of digital assets, making them prime targets for cyberattacks. The potential for significant financial profit attracts sophisticated cybercriminals, particularly in Decentralized Finance (DeFi).
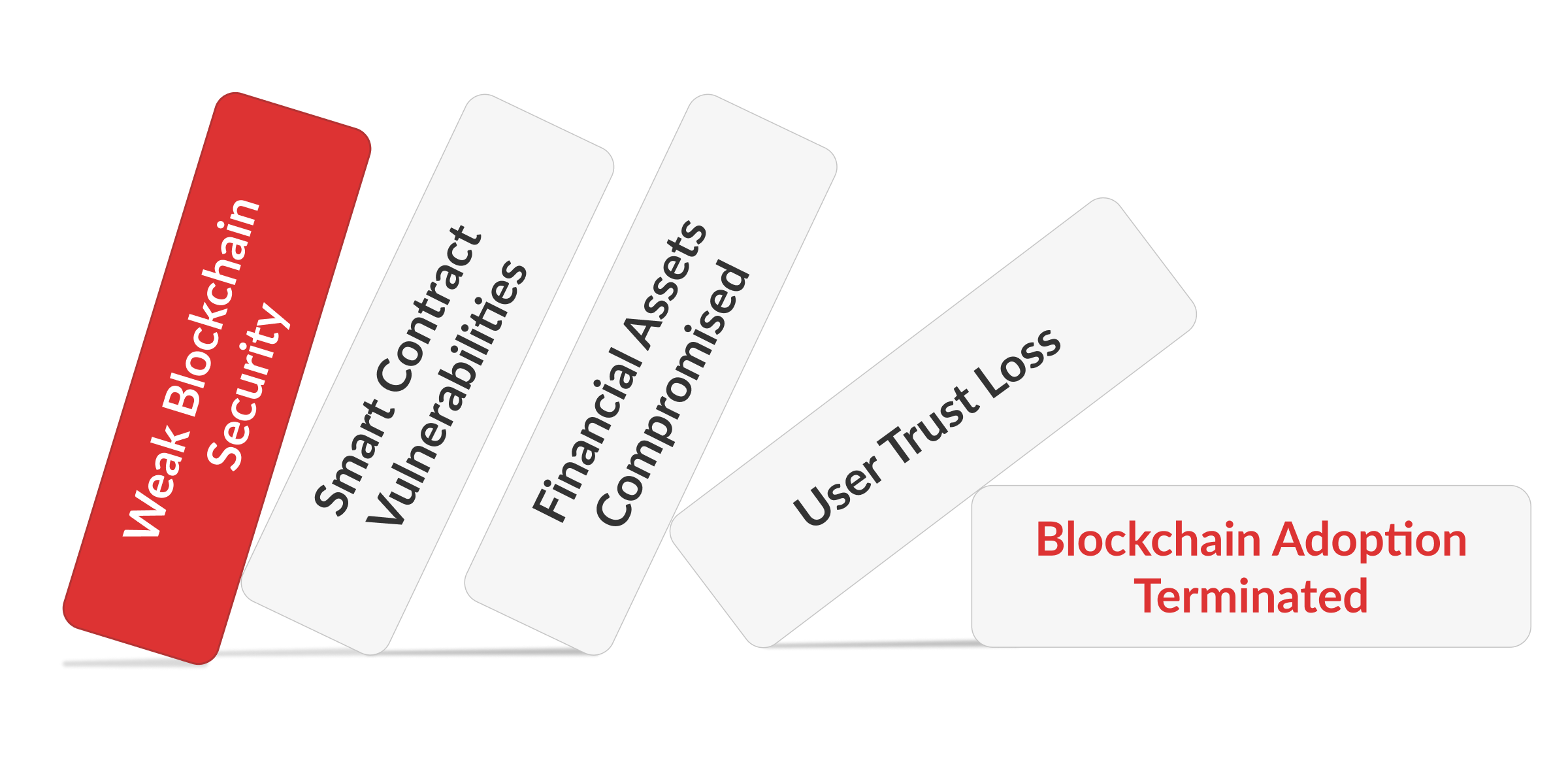
In this high-stakes environment, weak blockchain security is not merely a technical oversight; it’s an invitation to potentially catastrophic financial losses, where breaches can result in millions of dollars stolen in seconds.
Just recently, in February 2025, the Bybit exchange experienced a staggering $1.5 billion hack, the largest cryptocurrency theft in history. This attack, believed to be orchestrated by North Korean hackers, demonstrated that even supposedly secure “cold wallets” are vulnerable, highlighting the extreme financial risks in this space.
Trust in Decentralization
Blockchain technology’s revolutionary appeal lies in its decentralized model. Users’ confidence isn’t placed in central authorities, but in the integrity of a system’s code and underlying protocols.
Any blockchain vulnerabilities will directly sabotage this trust, which is the cornerstone of blockchain adoption and long-term sustainability. Security failures corrupt user confidence, potentially terminating broader acceptance as well as the growth of blockchain networks and applications.
Powerful Yet Risky Smart Contracts
Smart contracts, the self-executing code at the heart of many blockchain applications, are powerful tools for automation and decentralization. However, their complexity and intricate newborn development stages often lead to vulnerabilities. These vulnerabilities can often be too subtle or complex to detect through traditional methods, yet attackers use them and cause devastating effects.
Ensuring the safety of smart contracts through strict blockchain security solutions is vital. These solutions will prevent forced functionality while protecting users from financial and operational risks.
Balancing Transparency with User Privacy
While transparency is a core principle of blockchain, it also introduces potential privacy challenges. By design, all transaction data is publicly accessible, which can raise concerns about revealing sensitive user information.
Consider the 2023 Ledger data breach, in which nearly a million Ledger hardware wallet users’ personal information—including names, addresses, phone numbers, and email addresses—was revealed.
While the cryptocurrency remained secure on the blockchain, this user data breach highlighted the serious privacy risks when off-chain user information is linked to blockchain activity.
Strong blockchain data security protocols are crucial to balance transparency and privacy, safeguarding sensitive data, and preventing unauthorized access while maintaining the integrity of the blockchain.
Navigating the Regulatory Landscape
As blockchain technology matures and its impact broadens, the regulations will also naturally intensify, particularly around security and user protection. Compliance with emerging regulations isn’t just a legal necessity but a key factor in building trust during the long-term life of blockchain projects.
Secure development practices and safety measures are essential for navigating this evolving regulatory landscape, helping you avoid potential legal and financial consequences.
Key Blockchain Security Issues
While blockchain technology contains security features through decentralization and advanced cryptography, it’s still not immune to threats.
Proactively identifying potential blockchain security issues is crucial for protecting assets and preserving the foundational trust in blockchain systems. Let’s explore general blockchain vulnerabilities and how targeted testing strategies can effectively meet these risks.
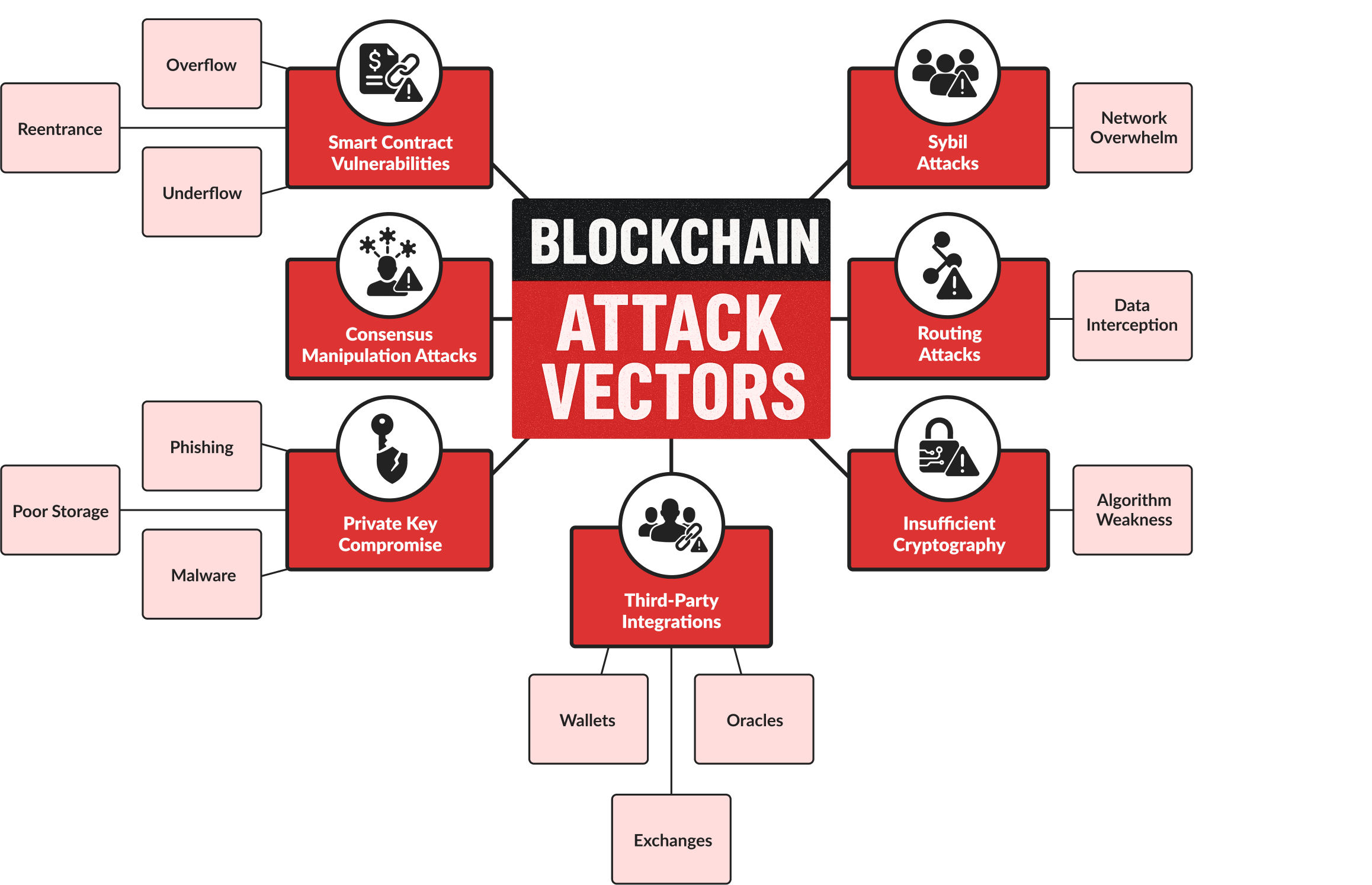
Smart Contract Vulnerabilities
Smart contracts are designed to automate transactions without mediators, but they’re often prime targets for attackers. Even minor bugs or logical errors in smart contract code can lead to unauthorized transactions, drained funds, or disrupted operations. The infamous DAO hack is a harrowing example of vulnerabilities in Ethereum’s smart contract code, leading to a substantial loss of funds.
Smart contract audits employ extensive code reviews by blockchain security experts, leveraging sophisticated tools like static analyzers and formal verification methods. They are essential to detect and fix these vulnerabilities, systematically checking for common issues such as reentrance attacks and overflow errors.
Undermining Consensus Attacks
Security for many blockchains relies on a consensus mechanism, often a Proof-of-Work or a Proof-of-Stake. This means a single entity or colluding group controls over 50% of the network’s mining power or stake.
In such a case, the entity or colluding group can potentially manipulate the blockchain. This control could possibly enable malicious actions, such as double-spending cryptocurrency or blocking legitimate transactions. Smaller blockchain networks, with less distributed mining or staking power, are sensitive to these risks.
Penetration testing, simulating sophisticated cyber-attacks, is crucial to assess a blockchain network’s resilience against 51% attacks and similar consensus mechanism manipulations.
Private Key Compromise
Private keys secure access to and control over blockchain assets. These cryptographic keys are the gateway to managing digital assets. If the associated assets are lost, stolen, or compromised, they become irretrievable. Common attack vectors include phishing schemes, malware infections targeting key storage, and flawed key management practices.
Rigid private key security assessments will evaluate the entire lifecycle of key generation, secure your storage, and confirm your management. These assessments are vital to prevent unauthorized access. They include security testing of hardware wallets, encryption techniques, and key recovery processes.
Sybil Attacks
In a Sybil attack, a single hacker attempts to subvert a decentralized network by creating many fake identities or nodes. By controlling many nodes, the attacker can gain influence over the network’s operations, potentially disrupting consensus mechanisms, manipulating voting processes, or launching denial-of-service attacks. Network security testing includes multiple simulations of Sybil attacks to evaluate the network’s ability to work under damaging conditions.
Routing Attacks
Blockchain networks rely on timely and accurate data propagation between nodes. Routing attacks use vulnerabilities in the network’s communication infrastructure to block and potentially alter data as it’s transmitted. Attackers might attempt to delay transaction propagation, manipulate orders, or add false information to the network.
Thorough network security testing is essential to analyze the network infrastructure for vulnerabilities to routing attacks and data interception. This testing focuses on validating the encryption of data in transit and the resilience of network nodes against various attack vectors.
Insufficient Cryptographic Protection
Blockchain security relies on the strength and integrity of cryptographic algorithms. However, cryptographic algorithms are not static; they can become vulnerable as new attacks are discovered.
Furthermore, even strong algorithms can become weak with inappropriate implementation. Cryptographic validation is a critical aspect of blockchain security. It involves rigid testing to verify the correct implementation of cryptographic algorithms and ensure they meet current and future security standards. This forward-looking approach is necessary to guard against appearing threats, including the potential impact of quantum computing on current cryptographic methods.
Expanding the Attack Surface
Blockchain applications rarely exist in isolation. They interact with external systems, including cryptocurrency wallets, exchanges, data oracles, and traditional APIs.
Vulnerabilities within these third-party integrations can create new entry points for attackers, compromising the entire blockchain application. Thorough integration testing, focused on blockchain security solutions, is necessary to evaluate the security of all third-party components and APIs.
Integration testing includes strict penetration and security testing of oracles, wallet integrations, and exchange interfaces to ensure they do not become weak links in the overall system.
Blockchain Testing: Our Strategies and Practices
We have more than 10 years of experience in blockchain testing and 16 years of tenure supporting various industries such as fintech, media & entertainment, e-commerce, and gaming. We know wholeheartedly that a successful blockchain testing strategy involves manual and automated testing, emphasizing security and performance.
Strategies for Manual Testing
Manual testing is essential for usability testing, exploring complex scenarios, and identifying subtle bugs. It is also helpful for testing user interfaces and functional testing.
For example, our Manual QAs found UX-related bugs in Trustee Plus, a financial app with a secure crypto wallet and a payment card.

Strategies for Automated Testing
Automated testing is vital for repetitive tasks, regression testing, and consistency. We often use automated tests for:
- Unit testing of smart contracts
- Performance testing
- Security scanning
Best Testing Practices
We reviewed and selected our most effective testing practices, which include the following:
- Early and Frequent Testing. Integrate testing throughout the development lifecycle.
- Comprehensive Test Coverage. Test all aspects of the blockchain application.
- Realistic Test Environments. Simulate real-world conditions.
- Security Audits. Conduct regular security audits by independent experts.
- Use Appropriate Tools. Use specialized tools and frameworks for blockchain testing.
- Collaboration. Foster collaboration between developers, testers, and security experts.
- Documentation. Maintain documentation of test plans, cases, and results.
Explore reputable cybersecurity resources like NIST, NSA, or CISA, as well as news portals like DarkReading and Krebs on Security, for additional insights into the evolving threat landscape.
As threats are constantly emerging and attack techniques are becoming more sophisticated, you’ll no longer be sufficiently supported by relying on regular security audits. Implementing continuous monitoring and integrating automated testing tools into the development pipeline is essential for proactive blockchain security. This approach allows the early detection of anomalies, regressions, and vulnerabilities.
Summing Up
Ensuring strong blockchain security is an ongoing process that demands careful attention at every stage of development. By implementing strict blockchain testing of services and protocols across all system layers—from smart contracts to network protocols—developers can identify and address blockchain security issues before hackers exploit them.
This commitment to broad blockchain testing is necessary to safeguard valuable digital assets, maintain critical user trust, and boost the secure adoption of blockchain technology.
To fortify your defenses and minimize vulnerabilities, consider further integrating essential services like penetration testing and security audits directly into your development lifecycle.
Proactively identifying weaknesses can help you build a strong and secure blockchain solution. When exploring these opportunities to strengthen your security, remember the expertise of specialized blockchain testing.
Our team at QAwerk offers comprehensive security testing to confirm your applications are resilient against threats. Whenever you’re ready to incorporate blockchain-powered security into your business, contact our experts for help.
See how we prepared to launch an encrypted social commerce app in only 3.5 months