Modern software development practices like Agile, DevOps, and CI/CD have revolutionized the software development landscape with automation and high speed. While this enables faster release cycles, it also opens the door to a plethora of security holes.
This article delves into software and data integrity failures, exploring common exploitations hackers use, real-life examples, and strategies for prevention.
Understanding Software and Data Integrity Failures
Let’s start with some background: Software and data integrity failures are listed in the OWASP Top 10 as the eighth most critical web application vulnerabilities. Also known as supply chain attacks, they represent a broad category of application security threats that occur when an application uses unverified components pulled from public repositories, untrusted sources, and content delivery networks.
Once a malicious operator breaches the network and sneaks inside, it’s easy to explore the system and make unauthorized changes. As a result, the system becomes susceptible to private information disclosure and even a system-wide compromise.
The consequences of software and data integrity failures extend beyond business disruptions, posing significant risks to both individuals and organizations. End-users often consume software and data from various sources without fully vetting them.
Examples of Software and Data Integrity Failures
Once malicious entities penetrate the system, they can do a whole bunch of damaging things. Let’s examine several examples of software and data integrity failures:
Continuous Integration / Continuous Delivery pipeline
A hacker can infiltrate the update distribution pipeline by inserting malicious code. If updates from this compromised source lack proper integrity checks, the malicious code can easily spread. Unwittingly, those implementing these updates promote disseminating harmful code from a trusted source, posing a significant security risk.
Insecure disposal
Old devices, such as computers, hard disk drives, and solid-state drives that have not been properly wiped, may expose users to data theft. Even a few leaked details can open the floodgates to malicious activities like identity theft, financial fraud, IP theft, and cyber fraud. It is of utmost importance to ensure that all sensitive data is completely removed.

Compromised pre-installed software
Attackers exploit vulnerabilities in pre-installed software to access sensitive data. If you’re using software secretly designed to collect and share sensitive information with cyber actors, you’re highly likely to become exposed to data theft. In either case, the data ends up in the wrong hands.
Addressing Software and Data Integrity Failures
Malicious actors are always on the hunt for security vulnerabilities and inevitably find a way in. Once they’ve breached a system, it’s crucial for organizations to promptly identify the intruders, remove them, and begin the cleanup process.
How do we identify and remediate software and data integrity failures? As a rule, this process involves the following consistent steps:
- Identify the root cause. This entails reviewing logs, studying network data, checking system configurations, and conducting forensic investigations to uncover security threats and track suspicious activity. This stage should happen as soon as possible to remediate without serious damage.
- Isolate infected systems and data before they reach the endpoint. Once the source of the failure has been identified, the affected files containing potential exploits must be quarantined to remove the opportunity for a threat actor to cause further damage.
- Correct the data integrity failure. Copying backup data from secondary storage, recovering corrupted files, or reentering incorrectly entered data would be the next best choice.
- Confirm that the affected data has been restored to its correct state. The power of remediation is simple and straightforward — run data integrity checks, compare data to previous records, and conduct validation tests. Verifying these things will give you an indication of the overall reliability of the system.
- Prevent further harm. Developing a sound security strategy, taking proactive security measures, and conducting staff training will prove its value. The key is not necessarily to outrun the bear but to outrun other hikers by making yourself a much harder target than other potential victims.
Real-Life Examples
Software and data integrity failures have been able to wreak havoc on major corporations. Let’s see how these attacks happened. Here are the most massive breaches of this kind in recorded history:
Equifax
A very famous example of a failure in software and data integrity checks is the Equifax attack in 2017. Bad guys exploited security weaknesses in Equifax’s systems, leading to the compromise of personal data for 148 million American consumers. This sensitive information included credit card details, names, phone numbers, addresses, birthdates, driver’s license numbers, and social security numbers.
This catastrophic data breach occurred because Equifax failed to update its public website with the latest version of Apache Struts and did not apply crucial security patches for a lengthy period. In the aftermath, Equifax, one of the three major US credit reporting agencies, faced numerous lawsuits, government investigations, financial losses, and a tarnished reputation.
SolarWinds
Probably the most high-profile example of this vulnerability would be the SolarWinds Orion supply chain attack from 2020. Sophisticated cyber actors gained access to a major US information technology firm’s software system by using methods like password spraying. Once inside, they stealthily added hacked code into the CI/CD pipeline of the targeted system. This rogue component was then incorporated into SolarWinds’ Orion software updates.
The company later distributed a malicious update to over 18,000 customers, which included government agencies and Fortune 500 companies. As customers installed the next software update for the Orion software, they unwittingly acquired the rogue component. Malicious operators exploited this window of opportunity to compromise email accounts, networks, and systems of some of the world’s largest corporations.
Prevention Strategies and Best Practices
Taking timely security measures prevents threat actors from achieving their goals. Let’s go over some best practices for preventing software and data integrity failures:
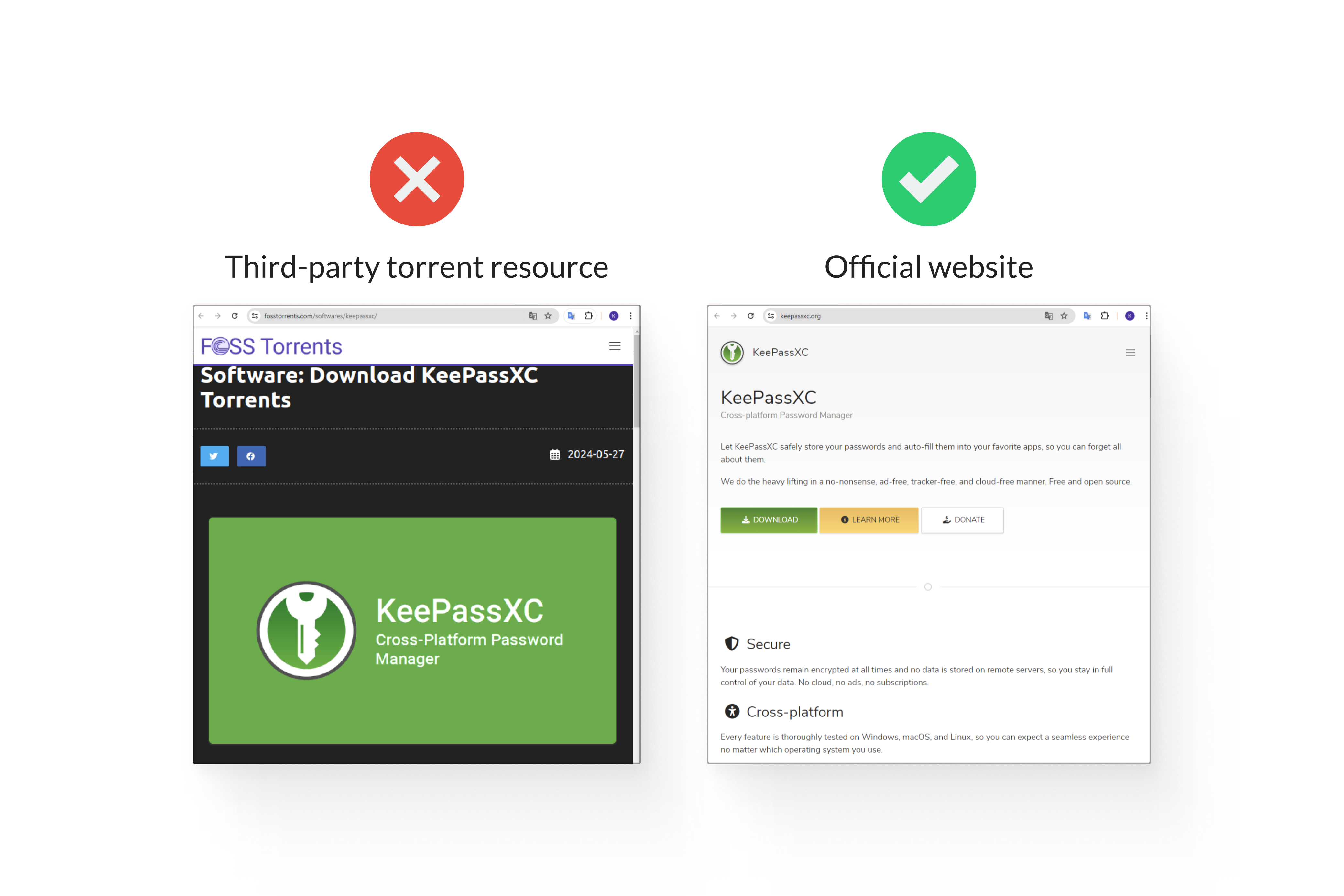
Download software components only from official sources
First and foremost, avoid unverified and pirated software components that may contain hidden vulnerabilities, malware, or backdoors, posing unnecessary risks to your environment. Malicious operators can easily compromise your system and data through these rogue components.
Use multi-factor authentication (MFA)
Multi-factor authentication provides an additional level of prevention. This defense mechanism makes it challenging for hackers to penetrate the network. Even if one critical security control is breached, attackers are still blocked from accessing or modifying the target resource because they need to overcome one or more additional barriers.
Conduct regular penetration testing
A promising approach to preventing attacks is to perform penetration testing. QAwerk conducts a comprehensive pentest, simulating web app attacks to identify weaknesses before ransomware criminals exploit them. Engaging with experts in penetration testing can maximize your opportunity to fix issues in a proactive manner.
Scan software for known vulnerabilities
Vulnerability scanning helps bolster your organization’s data protection strategy by ensuring that components do not include known vulnerabilities. Using vulnerability scanners early can prevent downstream issues, such as security misconfiguration, as well as potential server-side request forgery (SSRF) and insecure deserialization vulnerabilities.
Encrypt all sensitive data
Encryption is one of the most effective methods for minimizing unauthorized access. It safeguards your data at rest and in transit from hacker intrusions. Before sharing any sensitive data, it’s essential to encrypt it using security protocols like Transport Layer Security/Secure Sockets Layer (TLS/SSL).
Implement digital signatures
Code signing adds an additional layer of assurance. It guarantees the code’s integrity and protects your company and users from software tampering. This method allows developers to prove that a piece of software is authentic and verified by an electronic signature of a legitimate source.
Implement CI/CD pipeline segregation
Another effective method of eliminating the risk of a successful exploit of your business data is to decouple all development and deployment pipeline functions.
Decoupling removes direct dependence between components, services or systems, minimizing the risk of failure of one component affecting other components.
Having strong quality control and cybersecurity measures in place will help pass any data integrity assessment with flying colors.
How QAwerk Can Help With Software And Data Integrity Failures
Penetration testing is a powerful preventative security control that cannot be neglected, we must emphasize. QAwerk has a highly skilled and experienced team of pentesters who can significantly enhance your organization’s security posture.
At QAwerk, we employ best-of-breed security tools to simulate real-world attacks and assess the risk of unauthorized access to sensitive data. Our approach involves a blend of manual and automated testing across web, email servers, and hosting to evaluate security levels.
We conduct black, gray, and white box penetration testing to uncover security issues, data flow errors, and bugs. By combining these methods, we inspect both internal and external workings to identify all potential issues.
Final Thoughts
In summary, we’ve covered the basics of software and data integrity failures, how to identify them, and methods for fixing and preventing these issues.
As we saw with Equifax and SolarWinds, disregarding safety measures can result in catastrophic consequences. In both cases, cybercriminals went undetected within the victim network for months. Catching an attack in its early stages is far less disruptive compared to the massive effort required if intruders have found a way into your system a long time ago.
Without a thorough analysis, malicious operators can easily spread malware across your system under the cover of a regular update. Don’t let vulnerabilities put your organization at risk — reach out to professionals in the field.

