In the modern digital age, technology is part and parcel of our everyday lives. However, there are serious threats inherent in the use of web applications. Software risks can come from various sources, but one of the most prevalent is using vulnerable open-source or third-party components.
Although public open-source libraries, packages, and frameworks enhanced the modern software development process, the security gaps in components have opened the door to potentially malicious activities. Every day hackers find new devastating methods of exploiting vulnerabilities for personal gain.
If software developers use unsupported and out-of-date components, the software becomes susceptible to security vulnerabilities. Once you detect a vulnerability, the criminals may have already discovered it – and are actively working to leverage the flaw. How can hackers exploit this vulnerability, you may ask? This is exactly what we’re going to discuss here, among other things. So, let’s get started!
What are Vulnerable and Outdated Components?
If a software component is no longer maintained – it is considered a vulnerable and outdated component that can introduce serious security issues. Whether you are into app design or web development, you can write 100% secure code and still be exposed to vulnerabilities. The question arises: how is it possible? The answer is simple – through the use of vulnerable components.
If the components you use in the software building process are outdated, unpatched, or contain serious flaws, your organization, customers, and application users will become soft targets for hackers. Threat actors can leverage these flaws to take over the server, gain access to the application’s data, or compromise the system entirely. As software solutions change and evolve, there comes an urgent need for dev teams to update or replace components to prevent a potential security breach.
In 2017, using components with known vulnerabilities ranked ninth in the OWASP list of the ten most critical web application security risks. This issue moved from 9th place to 6th in the current OWASP Top 10 list.
Vulnerable and Outdated Components Attacks
Due to the growing number of vulnerabilities, there’s a high risk of inadvertently using unsupported or out-of-date components. Here are some practice examples of how using unsupported components can influence the security of your code. Ready to discover? Let’s go!
Outdated or vulnerable dependencies
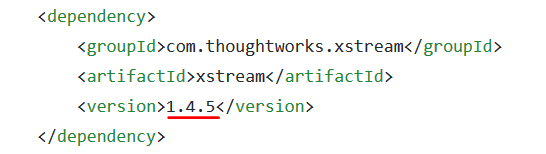
The reuse of unknown or untrusted components can lead to security vulnerabilities. For example, OWASP WebGoat employs a vulnerable Xstream open-source library version to convert an XML document into a Java object.
Pay attention to the library’s version – 1.4.5. It suffers from a high-severity deserialization vulnerability, which enables remote code execution (RCE) – one of the most severe attacks possible.
The code below will create the /tmp/here file on the docker container:
<sorted-set>
<string>foo</string>
<dynamic-proxy>
<interface>java.lang.Comparable</interface>
<handler class='java.beans.EventHandler'>
<target class='java.lang.ProcessBuilder'>
<command>
<string>touch</string><string>/tmp/here</string>
</command>
</target>
<action>start</action>
</handler>
</dynamic-proxy>
</sorted-set>
Malicious components and typosquatting
There are cases when software developers unintentionally use a malicious component similar to the legitimate one. This notion is called typosquatting – the practice of deliberately mistyping a famous name for malicious purposes. It is a widespread technique threat actors use to lure unsuspecting developers into downloading the malicious component.
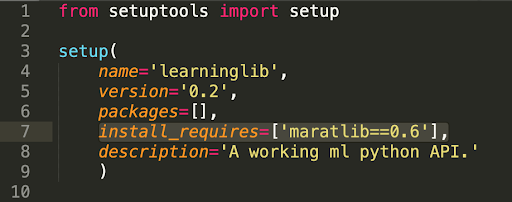
Examples are “maratlib”, “maratlib1”, “matplatlib-plus”, “mllearnlib”, “mplatlib”, and “learninglib” in PyPI (misspelling of the matplotlib legitimate Python plotting software). The other rogue components used the “maratlib” package as a direct dependency. In total, the malicious packages have reached almost 5,000 downloads.
Here is the case for the “learninglib” stated above:
Malicious operators continually target online code repositories such as PyPI (Python), NPM (JavaScript), and RubyGems, posing a major cybersecurity threat as developers may pull the malicious code into their projects without knowing. With typosquatting techniques, the bad guys can create compelling packages that might trick even knowledgeable developers.
Real-World Vulnerability Examples
Vulnerable and outdated components have led to grievous consequences for app users and severe reputational damage to companies. This vulnerability is a wide-open door through which intruders can easily penetrate the system and gain access to sensitive data. Here are the examples of the most devastating breaches caused by the OWASP A6:
Panama Papers
The Panama Papers is considered the largest breach ever in terms of the sheer volume of data leaked. Hackers stole the files from the computer systems of the Panamanian law firm and corporate service provider Mossack Fonseca. In 2016, it was the world’s fourth greatest company providing offshore financial services.
The leak of more than 11 million confidential documents, including 2.6 terabytes of information belonging to high-ranking politicians and public figures from more than 50 countries, was caused by the exploitation of outdated, unpatched versions of Drupal CMS and WordPress.
Ubuntu Forums
In 2016, perpetrators hacked a database of the Ubuntu Forums website. The bad guys leveraged the SQL injection flaw in the Forum Runner add-on for vBulletin, which had not yet been patched. By exploiting the vulnerability, they accessed the forum’s “user” table containing usernames, email addresses, and Internet Protocol addresses for 2 million registered users. Fortunately, malicious operators did not receive any valid user passwords.
The Canonical IT team has installed the ModSecurity web application firewall (WAF) to prevent similar cyber attacks and has brought vBulletin component vulnerabilities up to the latest patch level.
Equifax data breach
The Equifax data breach is one of the most famous hacker attacks related to using outdated and vulnerable components. In 2017, attackers took advantage of security lapses in Equifax’s systems. They compromised the personal information of 148 million American consumers, such as first and last names, phone numbers, home addresses, birth dates, driver’s license numbers, and social security numbers.
Equifax failed to update its public website with the latest version of Apache Struts. The company didn’t apply the appropriate security patches to remove a widely known vulnerability that allowed the breach to happen.
Detecting Vulnerable and Outdated Components
To detect the usage of outdated components that contain potential vulnerabilities, you have to fingerprint the technologies – collect the names, versions, and other specifics about the technologies the software employs. The techniques include:
- Analyzing HTML elements. As a rule, the HTTP traffic contains Cookies, Redirection URLs, Header values, HTTP status code information, and more. However, you can prevent unauthorized activity or identify unused network resources only if you know how to analyze this information. Thus, you can use browser extension tools to see the technologies used on websites you visit based on HTML page components and headers.
- Triggering errors. The practice of stressing the application and triggering verbose errors can give you a hint about the technologies employed. With the help of an automated software testing technique known as fuzzing, you can find coding errors and security loopholes by randomly feeding invalid, unexpected, or random data as inputs into an application.
- Forced browsing. This method aims to provide access to resources that are not linked with the application but are still present on the server. It allows you to search the domain directory for old configuration files, typical login portals, and README files containing information about the archive of computer software and possibly the name and version of the components.
- Source code. If you are authorized to access the application’s source code, check the list of dependencies to see the packages employed in the project.
Prevention & Mitigation
It’s crucial for organizations to be conscious of the risks of using vulnerable components and follow relevant guidelines to eliminate them. When it comes to cyber security – awareness is your best defense. Let’s explore some of the most effective preventive mechanisms. Here it goes!
Enable software composition analysis
Software Composition Analysis (SCA) is an automated process that deeply analyzes open-source packages incorporated into the software. With SCA, security experts can identify the risks and vulnerabilities associated with using third-party components brought into a project.
SCA tools provide a complete inventory of a project’s software assets: all components, their supporting libraries, as well as direct and indirect dependencies. SCA raises the developers’ awareness of security concerns and potential weaknesses, allowing them to create mitigation plans and take the necessary steps to prevent illicit activities.
Install Web Application Firewalls
Web Application Firewalls (WAFs) help protect websites and web applications by placing a protective shield between the system and the Internet that monitors HTTP traffic.
WAFs are a critical security defense against various attack vectors, including SQL injection, remote file inclusion (RFI), and cross-site scripting (XSS). With the right WAF in place, dev teams can inspect incoming traffic and block malicious HTTP requests before they reach the web application or user.
Even if your application, service or server is vulnerable, the WAF solution will not let “malicious requests” through.
Implement patch management process
IT professionals should formalize their approach to patch management to keep up with newly released security patches and enhance overall software performance. Proper patch management includes identifying and prioritizing patching needs, obtaining, testing, and installing patches to update or repair existing code.
Software programs, applications, and embedded systems tend to have technical problems that require timely fixes. Patches can be used to fix vulnerabilities, rectify errors, and plug security gaps.
Failure to update the components in time poses a significant security risk and leaves your operating systems vulnerable to malicious attacks. Moreover, it complicates future updates. Based on the number of projects built on the same vulnerable component version, the time required to run tests and apply patches would increase exponentially.
Conduct penetration testing
Penetration testing is a planned attack on an information system, where security experts take the same approach as an attacker to find weaknesses and critical vulnerabilities. By proactively hunting for vulnerable components, you can address cybersecurity issues and fix them before the system is deployed.
Penetration testing is one of the most efficient ways to keep your information system secure by continuous monitoring for web security vulnerabilities. Professional pentesters at QAwerk use advanced tools to examine the target applications for weaknesses and protect organizations from unwelcome attempts to access their computer systems.
How to Combat #6 OWASP Vulnerability?
Dev teams and security managers require defensive measures to impede malicious activity and ensure their organization is not left open to cybersecurity threats. The most practical ways to address component-based vulnerability include the following:
- Rely on OWASP, SANS/CWE, and CERT coding standards to improve software performance and reduce vulnerability exposure.
- Implement automated alert and patching tools to ensure a secure software development lifecycle (SDLC) process and give your dev teams a snapshot of potential flaws.
- Keep a comprehensive inventory of all components used in the application to ensure only approved elements are in place. Continuously review and update the list.
- Prefer signed packages to minimize the risk of including a changed, harmful component.
- Eliminate deprecated or unused components, items, folders, features, and redundant dependencies to lessen the possibility of security flaws.
- Regularly scan libraries, components, and their dependencies to detect weaknesses.
- Include components only from official sources via secure links and verify to ensure compliance with legal standards and regulations.
In Conclusion
Today’s world runs on technology. Software applications, solutions, and platforms touch almost every aspect of our lives. Yet, they also come with security risks that create a window of opportunity for attackers to cause serious problems to application users and organizations, even to big and well-known ones.
Incidents occur, but if you’re well-informed and prepared, you can do a much better job of dealing with web security vulnerabilities. For this reason, dev teams must sharpen their focus on the highly exploitable, high-impact vulnerabilities and follow secure software development practices.
Knowing about the vulnerabilities as early as possible helps security practitioners understand the issue and craft the most secure fix. Software developers must take proactive measures to mitigate the risks, avoid malicious attacks, and prevent breaches against the organization.

