- July 19, 2024
- 6 min read
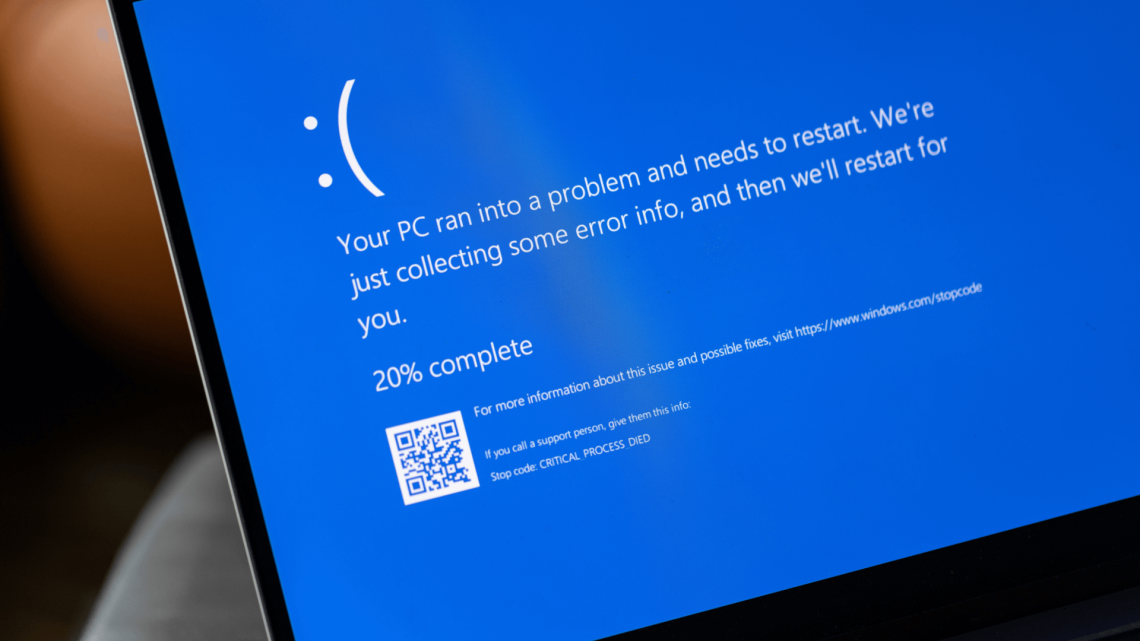
Just yesterday, the idea that a single IT misstep could cripple companies across entire industries might have seemed like a huge overstatement. However, the recent Microsoft outage is a stark reminder of how interconnected our world is. On July 19th, 2024, a faulty security update from CrowdStrike wreaked havoc on Microsoft Windows systems worldwide. How could such an IT catastrophe unfold? Let’s dive in and explore the causes.
- July 4, 2024
- 10 min read
No one likes reporting on data breaches and reassuring their customers that their data is still in safe hands. That’s why businesses should take proactive actions to enhance their security posture, avert cyberattacks, or at least minimize their damage.
- July 3, 2024
- 8 min read
Modern software development practices like Agile, DevOps, and CI/CD have revolutionized the software development landscape with automation and high speed. While this enables faster release cycles, it also opens the door to a plethora of security holes.
- June 24, 2024
- 10 min read
In this age of increasing cyber threats, the security of web applications has become a paramount concern. Malicious entities are always on a lookout for new opportunities like lack of logging and monitoring. They spend a lot of time examining applications and systems to find errors and vulnerabilities.
- December 11, 2023
- 8 min read
Every day, thousands of new vulnerabilities emerge, creating new opportunities for hackers. The bad guys don’t take breaks or vacations! They are actively working to compromise your systems.
- July 17, 2023
- 11 min read
In the modern digital age, technology is part and parcel of our everyday lives. However, there are serious threats inherent in the use of web applications. Software risks can come from various sources, but one of the most prevalent is using vulnerable open-source or third-party components.
- March 17, 2023
- 13 min read
We live in the era of rapid digital transformation with innovative solutions allowing us to perform a wide range of things faster and easier. As technologies continue advancing, hackers and threat actors create sophisticated counter-approaches by exploiting these futuristic technologies.
- November 30, 2022
- 11 min read
August 6, 1991. Does the date ring any bells? No, it wasn’t the collapse of the Soviet Union (though you’re close). It was on that otherwise unremarkable summer day that Tim Berners-Lee launched the very first web page. More than thirty years have passed since then, and websites have come a long way, haven’t they?
- November 9, 2022
- 12 min read
The internet is NOT a safe place. Wonderful in its own right, sure, and useful in more ways than one. But the cyberspace is also filled to the brim with malicious agents: thieves, hackers, countless different criminals looking to prey on the weak and the vulnerable. Don’t be alarmed just yet though. As long as
- November 4, 2022
- 11 min read
They say that programming is the closest thing to magic that we have today. And you know what? They’re right. A few lines of code that look like nothing but gibberish to the uninitiated – and you can create entire worlds. How is it anything but magic? On the opposite side, a few different lines